It’s strange – we have great new tools, but many folks are using them in such a sloppy way, that the tools get discredited. And this also tends to boil down that serious users get into trouble. You probably guess what I am talking about: AI tooling.
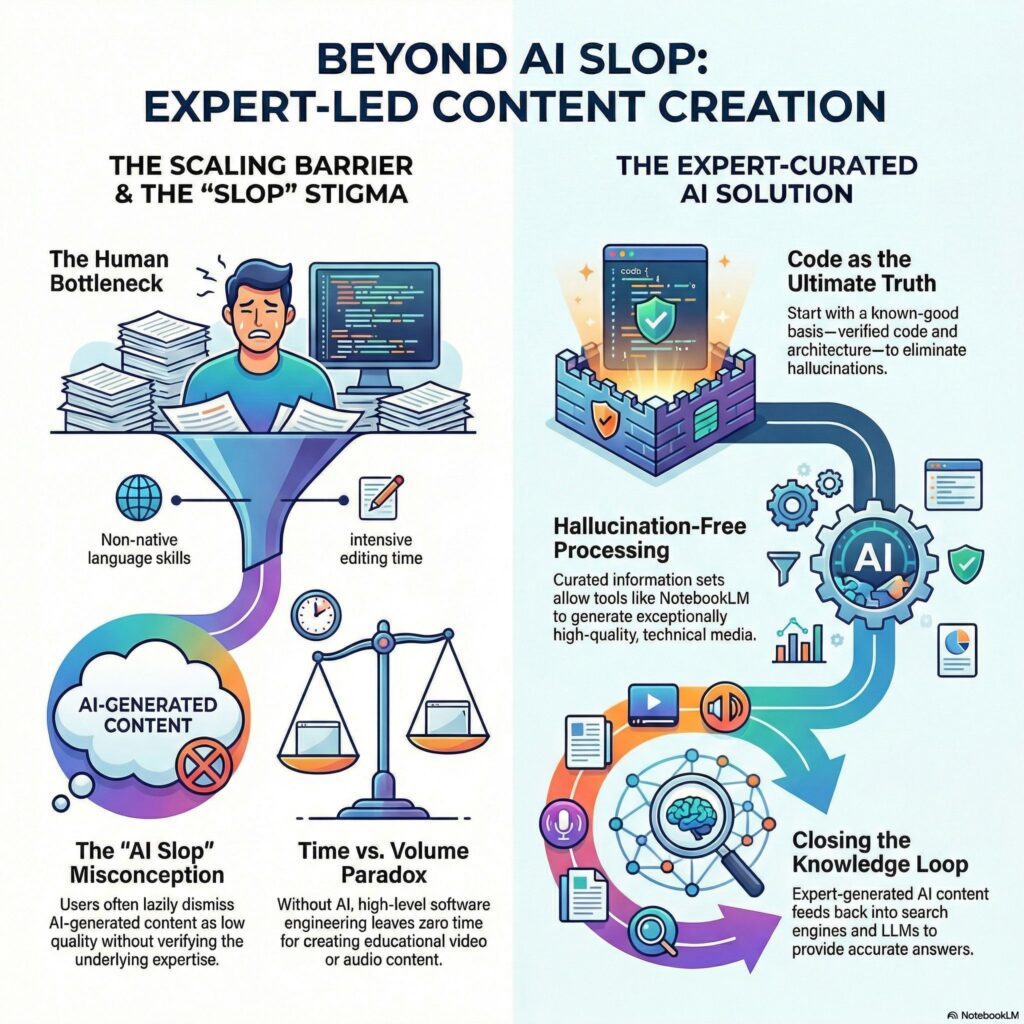
I am for sure nobody who jumps on the latest hype. So I resisted AI quite long for complex things. Until it was ready, which for me was around summer 2025. That was for coding. For some doc writing it was ready earlier (and I used it to cover my weak spots). Now, AI has evolved to also help with video and audio.
Continue reading “AI Slop – or Human Laziness?”